In our interconnected world, computer networks have become the backbone of modern communication. From simple home setups to complex global infrastructures, networks enable the seamless exchange of information that powers our digital lives. However, the physical connections between devices whether wireless signals or physical cables are just the beginning. For true communication to take place, devices need a shared understanding of “how” to communicate with each other.
The Essential Elements of Communication
Whether we’re talking about human conversation or computer networks, all forms of communication share three fundamental components:
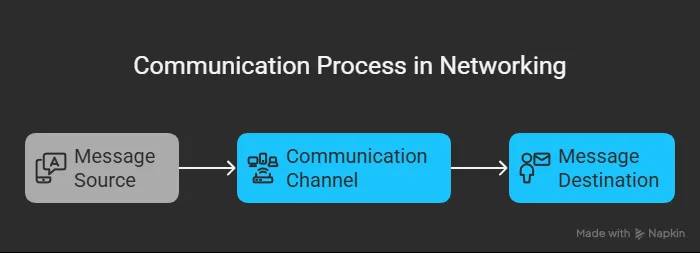
The Message Source (Sender)
This is the starting point of communication the device or person that initiates the exchange by sending information. In networking terms, this could be your smartphone sending a text message, a laptop uploading a file, or a server delivering a webpage.
The Message Destination (Receiver)
On the other end of communication is the receiver the entity that the message is intended for. The receiver’s job is to accept the incoming message and correctly interpret its meaning. In networks, this might be another person’s phone receiving your text, a cloud storage service accepting your uploaded file, or your browser displaying a webpage.
The Communication Channel
Between sender and receiver lies the channel the pathway that carries the message from its origin to its destination. In networking, this channel consists of the physical media (such as copper wires, fiber optic cables, or wireless radio waves) as well as the infrastructure (like routers and switches) that guide the data along its journey.
Network Communication Protocols: The Rules of Digital Conversation
Just as human conversation follows certain rules of etiquette and language, network communication relies on established protocols. These protocols are essentially agreements about how devices should format, transmit, and process information when communicating with each other.
The Importance of Standardized Rules
Consider what happens when communication rules are broken. If you received this message:
“networks communication between govern protocols. It is verydifficult tounderstand messages that are not properly structured and donot follow the established conventions and rules.”
The meaning gets lost in the poor formatting and structure. Similarly, computer networks would fail without clear, shared protocols that all connected devices understand and follow.
When properly formatted according to agreed-upon rules, the message becomes clear:
“Protocols govern communication between networks. It is very difficult to understand messages that are not properly structured and do not follow the established conventions and rules.”
Key Requirements for Network Protocols
For networks to function effectively, their protocols must address several critical requirements:
Clear Identification of Sender and Receiver
Every message in a network needs addressing information who is sending the message and who it’s intended for. This is similar to writing an address on an envelope before mailing a letter.
Common “Language” and Structure
Communicating devices must use compatible formats and structures that both sides understand. This includes everything from the basic encoding of binary data to the organization of information within data packets.
Precise Timing and Delivery Controls
Networks need rules about when and how quickly information is sent, as well as what happens if messages are delayed or lost.
Verification and Acknowledgment Systems
Many network communications require confirmation that messages have been received correctly, similar to requesting a delivery receipt for an important package.
The Technical Requirements of Network Protocols
When we look deeper at how network protocols function, we can identify six essential technical requirements that enable successful digital communication:
1. Message Encoding: Translating Information for Transmission
Encoding is the process of converting information into a format suitable for transmission across network media. When you send an email, for example, your message is converted into bits (1s and 0s) before being transmitted.
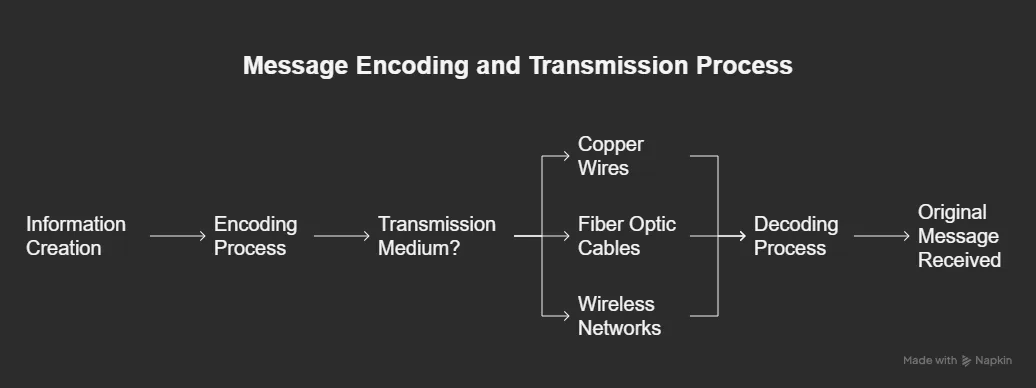
Different transmission media require different encoding methods:
- On copper wires, bits are represented by electrical voltage patterns
- In fiber optic cables, they become pulses of light
- In wireless networks, they’re encoded as radio or microwave signals
The receiving device must then decode these signals to reconstruct the original message. This encoding/decoding process happens billions of times daily across global networks, usually without users even being aware of it.
2. Message Formatting and Encapsulation: Packaging Data for the Journey
Network protocols define specific structures for organizing data. This formatting is crucial for devices to properly interpret the information they receive.
Encapsulation is a key concept here it’s the process of placing data within a specifically structured container (a packet or frame) that includes all necessary addressing and control information. Think of it like placing a letter in an envelope with the proper address and return information.
The Internet Protocol (IP) serves a function similar to an envelope in postal mail. IP packets contain fields that identify their source and destination addresses, allowing routers to forward them correctly across networks. These packets can travel through multiple networks and devices before reaching their final destination, with each intermediary device reading the addressing information to determine where to send the packet next.
3. Message Size: Breaking Down Information into Manageable Chunks
Networks impose strict limitations on how much data can be transmitted in a single frame. These size restrictions serve several purposes:
- Preventing any single communication from monopolizing network resources
- Reducing the impact of transmission errors (smaller frames mean less data needs to be retransmitted if errors occur)
- Allowing fair access to the network for all connected devices
When you send a large file across a network, the sending device first breaks it into numerous smaller frames that comply with size requirements. Each frame contains:
- A portion of the original message
- Addressing information identifying its source and destination
- Control information for error checking and sequencing
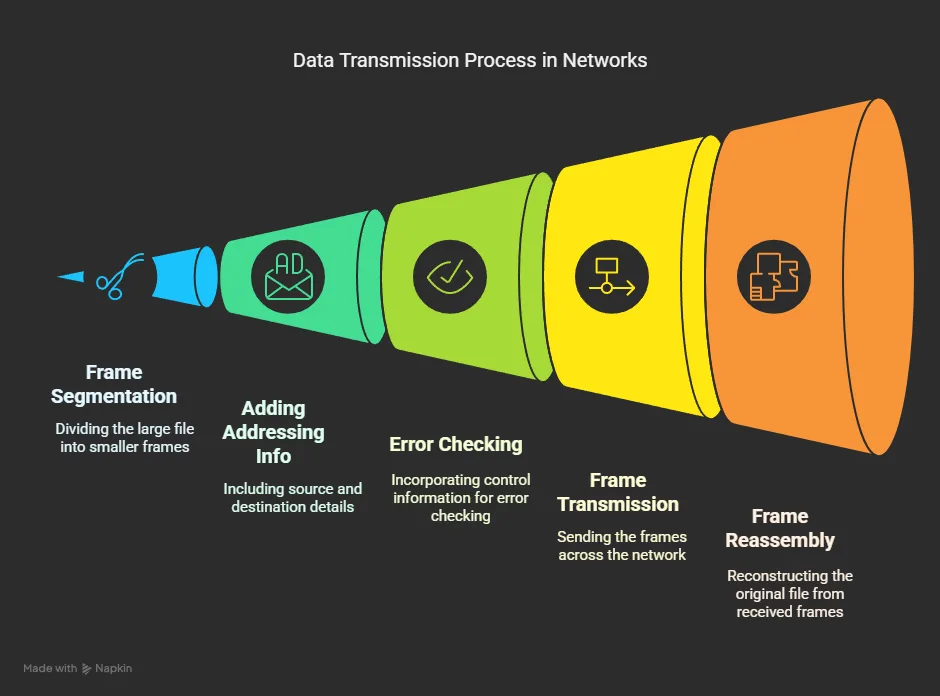
At the destination, these individual frames are reassembled in the correct order to reconstruct the complete message. This process is invisible to end users, who simply see their file being sent or received.
4. Message Timing: Coordinating the Flow of Information
Timing is critical in network communications and encompasses several important concepts:
Flow Control
Flow control regulates the rate and volume of data transmission to prevent overwhelming the receiver. If data arrives faster than a device can process it, information may be lost or corrupted. Network protocols include mechanisms for devices to negotiate suitable transmission rates and pause transmission when necessary.
For example, if a server is sending data to your smartphone faster than your phone can process it, flow control mechanisms allow your phone to signal “slow down” to the server.
Response Timeout
Networks need rules for how long a device should wait for a response before taking action. If a device sends a message and receives no acknowledgment within the specified timeout period, it might:
- Assume the message was lost and retransmit it
- Try an alternative path if available
- Report an error to the user or application
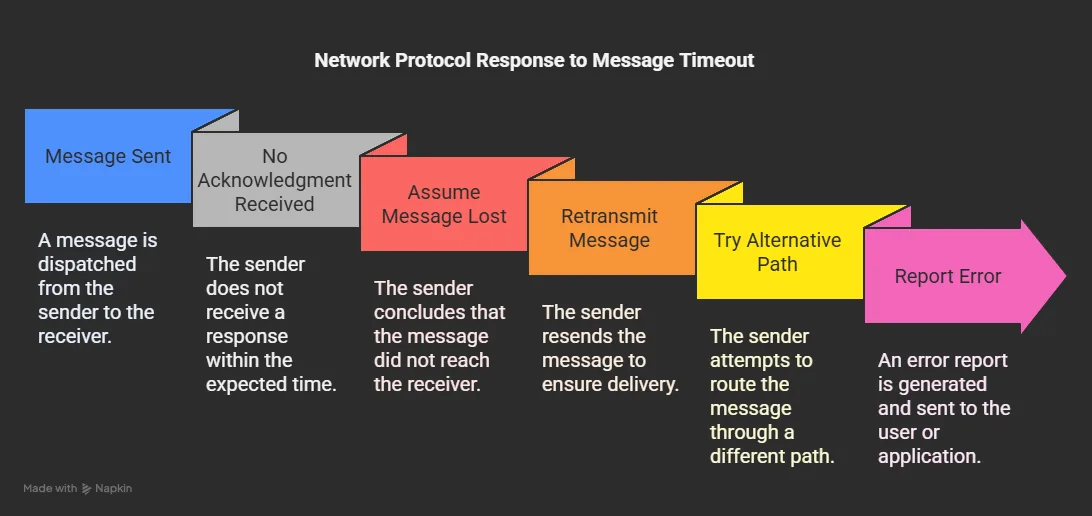
Without proper timeout mechanisms, applications might hang indefinitely waiting for responses that never arrive.
Access Method
Access methods determine when devices are permitted to transmit data on a shared medium. These methods prevent multiple devices from transmitting simultaneously, which would cause their signals to interfere with each other (known as a collision).
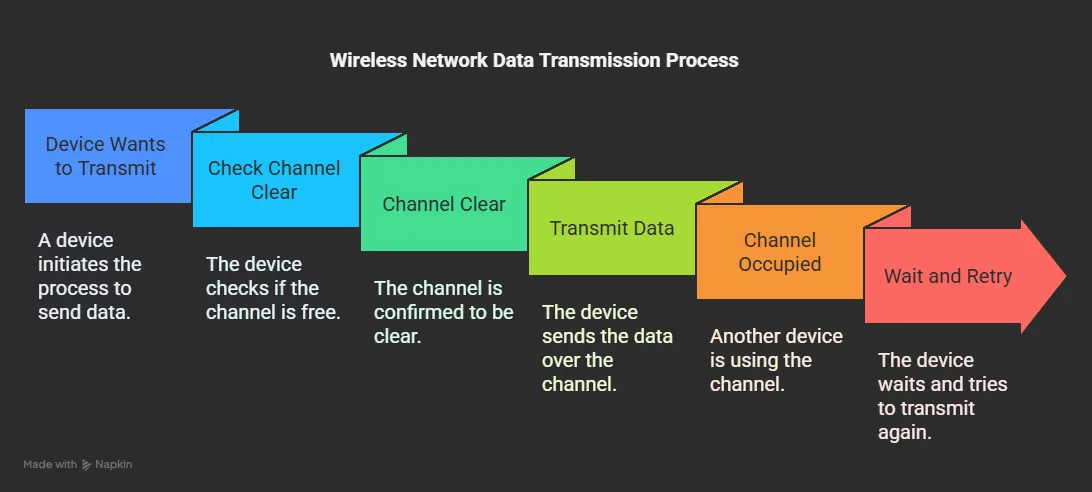
For instance, in wireless networks, devices must first check if the wireless channel is clear before transmitting. If another device is already using the channel, the device must wait and try again later.
5. Message Delivery Options: Reaching the Right Audience
Network protocols support different communication patterns depending on what kind of audience needs to receive the information:
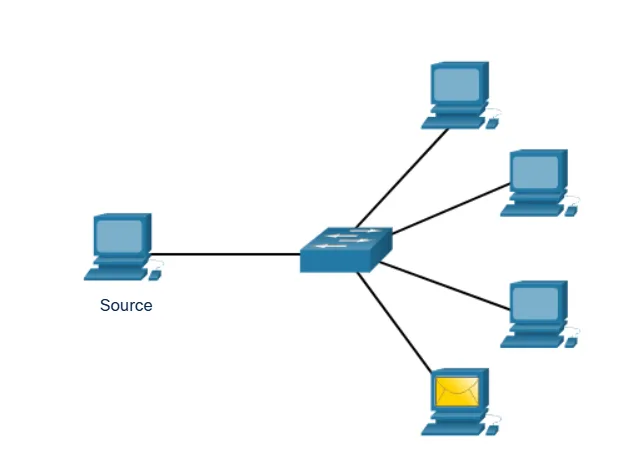
Unicast Communication
In unicast delivery, information travels from one source to a single, specific destination. This is the most common form of network communication, used whenever you visit a website, send an email, or stream a video. The data packets contain specific addressing information that identifies exactly which device should receive them.
Multicast Communication
Multicast enables a single device to send information to a selected group of devices simultaneously. Rather than sending individual copies to each recipient, the source sends a single stream of data that is replicated by the network only where paths diverge.
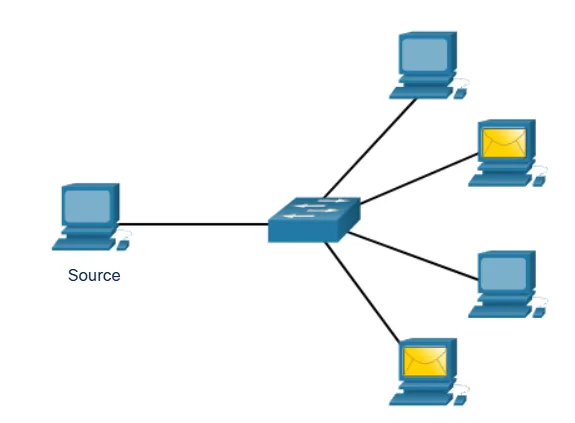
This method is particularly efficient for applications like:
- Video conferencing, where multiple participants receive the same video stream
- Live streaming events to many viewers
- Distributing software updates to specific groups of computers
Broadcast Communication
Broadcast communication sends information to all devices within a network segment. It’s used when information needs to reach every device on the local network, such as:
- Network discovery processes
- Address resolution through ARP (Address Resolution Protocol)
- Certain types of network configuration information
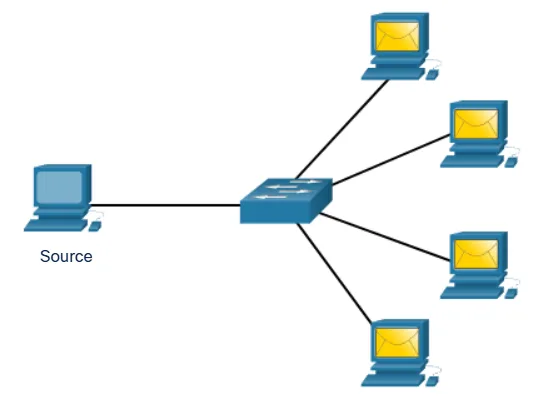
Broadcast is limited to local network segments and is not forwarded across the broader internet to prevent overwhelming the global network with unnecessary traffic.
The Layered Approach to Network Communication
Modern networks implement communication protocols in layers, with each layer responsible for specific aspects of the communication process. This layered approach—often represented by the OSI (Open Systems Interconnection) model or the TCP/IP model provides several advantages:
- Simplifies complex processes by breaking them into manageable components
- Allows different protocols to handle specialized functions
- Enables technology evolution at one layer without requiring changes to other layers
For example, when you browse a website, different protocol layers handle:
- The physical transmission of electrical signals (Physical layer)
- Error detection in the received data (Data Link layer)
- Routing across multiple networks (Network layer)
- End-to-end connection management (Transport layer)
- The web browsing session itself (Application layer)
The Impact of Effective Network Communication
Well-designed communication protocols enable the reliable, efficient network operations we depend on daily. When these protocols function correctly, users experience:
- Consistent connection quality
- Reliable data delivery
- Efficient resource utilization
- Seamless interaction between different types of devices and networks
As networks continue to evolve, with technologies like 5G, IoT (Internet of Things), and edge computing becoming more prevalent, communication protocols adapt to meet new requirements for speed, security, and connectivity.
Understanding network communication fundamentals reveals the sophisticated mechanisms working behind even our simplest online interactions. From the basic elements of senders, receivers, and channels, to the complex protocols governing data exchange, networks rely on carefully designed rules and structures to function effectively.
These communication principles apply across all network types from the smallest home network to the global internet infrastructure. By establishing common protocols for encoding, formatting, sizing, timing, and delivering messages, networks create the universal language that allows our increasingly connected digital world to function.
As you connect to websites, send messages, or stream media, remember that beneath these seemingly simple actions lies an intricate dance of protocols ensuring your data reaches its destination accurately and efficiently. The invisible rules of network communication form the foundation of our modern digital experience, enabling the connections that power our connected world.
What’s the difference between unicast, multicast, and broadcast communication?
These three terms refer to different methods of delivering messages across a network:
Unicast sends information from one source to one specific destination device. This is the most common form of network communication, used when you browse websites, send emails, or chat with a single person.
Multicast sends information from one source to a select group of destination devices simultaneously. Rather than sending individual copies to each recipient, the network efficiently delivers a single data stream that splits only where necessary. This is commonly used for video conferencing, live streaming events, and software updates to specific groups.
Broadcast sends information from one source to all devices within a network segment. Every connected device receives the message regardless of whether they need it. This method is used for network discovery, address resolution, and sharing network configuration information, but is limited to local networks to prevent overwhelming the broader internet.
Why do networks break large files into smaller pieces when sending them?
Networks impose strict size limitations on data frames for several important reasons:
Error management: If a transmission error occurs in a smaller frame, only that small portion needs to be retransmitted, not the entire file. This is more efficient than resending a large amount of data.
Fair network access: Breaking data into smaller units prevents any single communication from monopolizing network resources for too long, ensuring all connected devices get a fair opportunity to transmit their data.
Reduced latency: Smaller frames allow for more responsive interleaving of different communications across shared network infrastructure.
Compatibility: Different network technologies have different maximum frame sizes based on their design and physical limitations.
When you send a large file, your device automatically handles this fragmentation process, breaking the file into appropriate-sized chunks, each with its own addressing information. At the destination, these pieces are reassembled into the complete original file without you needing to manage this process.
What is protocol encapsulation and why is it important?
Protocol encapsulation is the process of packaging data by wrapping it in layer-specific protocol information as it travels through the network stack. Think of it like putting a letter inside an envelope, then putting that envelope in a shipping box, and finally adding a shipping label.
In networking:
1. Your original data (like an email message) starts at the application layer
2. Each network layer adds its own header information (and sometimes trailer information)
3. By the time your data reaches the physical layer, it has been encapsulated multiple times with all the necessary addressing and control information
Encapsulation is crucial because it:
1. Allows different network layers to function independently
2. Makes sure data carries all the information needed for successful delivery
3. Enables networks to route information correctly across complex paths
4. Provides mechanisms for error checking and security
5.Allows the receiver to properly process and interpret the data
This layered approach means each protocol only needs to understand its specific responsibilities, making networks more flexible and easier to develop.
How do devices know when they can transmit data on a network?
Devices use various access methods to determine when they can safely transmit without interfering with other communications. The specific method depends on the network type:
For wired Ethernet networks:
Modern switched networks use full-duplex communication where each device has a dedicated connection to the switch, allowing simultaneous sending and receiving without collision concerns
Older shared Ethernet networks used CSMA/CD (Carrier Sense Multiple Access with Collision Detection), where devices would listen before transmitting, stop if a collision was detected, and retry after a random wait time
For wireless networks:
1. Devices use CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance)
2. Before transmitting, a device checks if the wireless channel is clear
3. If the channel is busy, the device waits a random amount of time before checking again
4. Additional mechanisms like RTS/CTS (Request to Send/Clear to Send) help manage the “hidden node problem” where two devices can’t detect each other but both can reach the access point
These access methods ensure orderly communication and prevent data corruption from signal collisions, which is especially important in shared media environments.
What happens if a message doesn’t reach its destination in a network?
Networks implement several mechanisms to handle failed message delivery:
Timeout and retransmission: The sending device waits for an acknowledgment within a specific time period. If no acknowledgment arrives, it assumes the message was lost and retransmits it, often multiple times before giving up.
Error reporting: After multiple failed attempts, the sending device or intermediate network equipment may generate error messages (like ICMP “Destination Unreachable” messages) to inform the source about the delivery problem.
Application notifications: End-user applications typically receive notifications about communication failures and may display messages like “Connection timed out” or “Server not responding.”
Alternate routing: Some protocols can dynamically find alternative paths through the network if the primary path fails.
Graceful degradation: Many applications implement fallback mechanisms to function at reduced capability when full communication isn’t possible.
The exact recovery process depends on the specific protocols being used. For example, TCP provides reliable delivery with acknowledgments and retransmissions, while UDP is connectionless and doesn’t guarantee delivery, placing responsibility for handling lost messages on the application itself.